
The roles of the service provider and customer in cloud security
Cloud computing can be traced back to the 1950s (with its ancestors, mainframe computing and time sharing, and the later development of virtualisation). It really took off with the advent of high-speed, broadband Internet connection during the first decade of the 2000s and has since been growing exponentially. As the market gains ever more popularity, Mathieu Weber and Jarry Xiao of TekID look into the issues surrounding cloud security.
According to Gartner, the global cloud computing market totalled United States dollars (USD) 182.4 billion in 2018 and is expected to reach USD 249.8 billion in 2020.[1] The reason for this unprecedented growth is that more and more companies, big and small, are migrating from on-premise to cloud solutions (such as workload, communication, supply chain, Office 365 and Dropbox.). This is due in particular to the cost-effectiveness, ease of scaling-up, flexibility and almost unlimited resources and options of cloud computing. Currently, AWS (Amazon Web Services) still dominates with 47 per cent of public cloud market share at the time of writing, followed by Microsoft Azure with 22 per cent and Aliyun with eight per cent.[2]
If cloud solutions become standard, many companies will mainly consider the pros and ignore the cons when making the switch. While cloud computing indeed offers numerous advantages, the risks—which may arise if the service is not managed or controlled properly—must also be acknowledged.
What is cloud?
In simple terms, cloud is the delivery of computing services, resources and power (such as servers, storage, software, applications, databases, networking and analytics.) over the Internet, instead of through on-premise infrastructure or a computer hard drive. The main purpose of a cloud is to allow companies to perform tasks faster and more securely, while getting rid of often huge and costly server infrastructures.
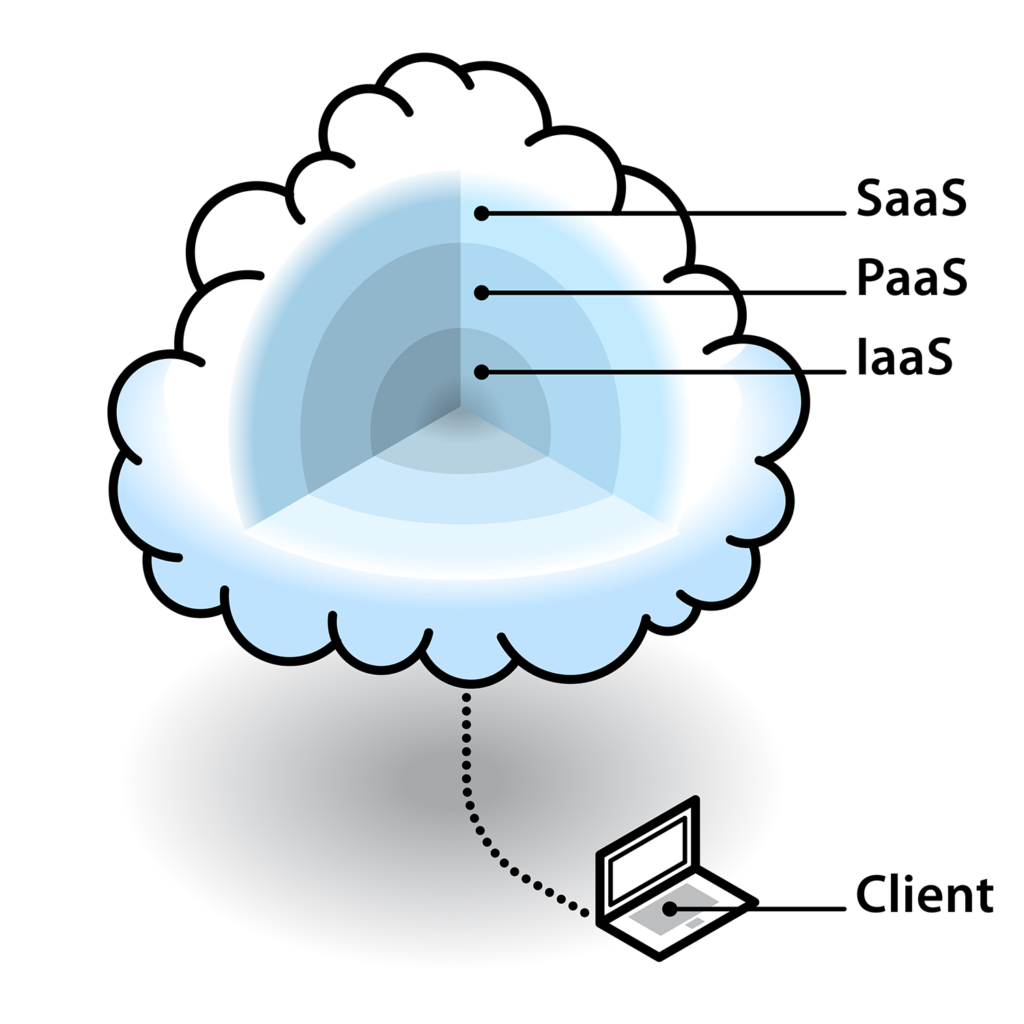
There are three major cloud models: IaaS (Infrastructure as a Service), PaaS (Platform as a Service), and SaaS (Software as a Service).
- IaaS gives you access to pre-configured hardware via a virtual interface and lets you manage your applications, runtime, middleware and operating system and data, by yourself.
- PaaS gives you access to a platform and lets you develop, run and manage applications without the complexity of building and maintaining the infrastructure.
- SaaS gives you access to a software (together with its maintenance and support) and lets you enjoy its service.
The SaaS model is understandably the most popular, as companies don’t have to worry about the technical side and can instead fully focus on their core business.
Today, most cloud providers use a ‘pay as you go’model, which has proved extremely effective as it fits the needs of both small vendors and business giants: no flat subscription – customers only pay for what they use.
One can test different cloud service providers (as they often offer a trial period) before making a final decision. However, before migrating to a cloud, one still must take into account the associated security risks.
Who is responsible for cloud security?
“If people say, ‘if I sign with you, can you guarantee I won’t be hacked?’ If I say yes, I’m lying,”
Microsoft’s top cloud executive Scott Guthrie.[3]
Further illustrating this point, a growing number of staggering Cloud data breaches and related vulnerabilities have come to light in recent years, but who should be blamed? In most cases, such data breaches are due to misconfiguration or incorrect access control, despite cloud providers’ commitment to security accompanied by dedicated security teams and regular vulnerability patches.
In fact, most risks originate from customers’ lack of cloud security awareness. For example: in 2017, personal data on 198 million American voters was leaked due to the database being unintentionally made accessible to everyone on an open Amazon S3 storage server by the cloud customer.
“Through 2022, at least 95 per cent of cloud security failures will be the customer’s fault.”
Jay Heiser, research vice president at Gartner, [4]
Cloud security is everyone’s business and cannot be shifted exclusively to the cloud provider: cloud customers also have a critical role to play.
What can cloud customers do to secure it?
The following are the basic minimum measures to put in place:
- Even in a cloud, encrypt your data: Encryption is way under-rated, yet this method ensures the confidentiality, integrity and security of your data even if there’s a breach, as it cannot be read or used when encrypted. However, even in the first half of 2018, only three per cent of all data breaches were ‘secure breaches’, i.e. where encryption was used.[5]
- Adopt a secured encryption key management service: While encryption can be a very effective method to maintain confidentiality, integrity and security, if the private key is not properly stored (or is leaked or stolen), all these efforts become useless. Almost all cloud service providers have a key management service you can use.
- Implement strict access control rules: For cloud services, user segmentation must be set up, with roles and ‘principle of least privilege’ – i.e. limiting access to the strict minimum the end-user needs to perform their work.
- Back up your data: Implementing encryption and access control may not prevent data loss, which can be permanent unless you have back-ups, with disastrous consequences for your business.
- Secure your application programming interfaces (APIs): They are likely to be the entry points of attackers. Perform regular penetration tests and patch any discovered vulnerabilities.
- Perform a cloud provider due diligence: Verify the security credentials of your cloud provider.
What is the impact of the European General Data Protection Regulation (GDPR) and of the China Cybersecurity Law (CSL) on cloud security?
Both the GDPR and the CSL are technology neutral, in that they are applicable to all any and all types of technology, whether existing or future (and therefore apply to cloud computing). Both provide for the mandatory adoption of technical and organisational security measures.
It’s been a year since the GDPR came into effect and two years for the CSL, and though it’s still too early to assess if they have helped reduce the number of data breaches, they have however forced companies to start taking stock of and patching their security vulnerabilities.
More generally, more and more laws to regulate cybersecurity and data processing are taking effect across the globe, all providing for security obligations. This should have a positive effect by underlining that noncompliance can lead to very serious legal consequences and fines, on top of huge financial losses ensuing from business disruption. For example, on 8th July 2019, British Airways was slapped with a USD 230 million fine by the Information Commissioner’s Office (equating to 1.5 per cent of its worldwide turnover for 2017), due to a data breach in 2018 that ended in some 380,000 customers’ credit card data being stolen.[6]
In brief
A company moving to the cloud without carefully considering and tackling the risks involved exposes itself to a multitude of security, technical, legal, compliance, commercial and financial risks. And in cloud computing, the responsibility for security and mitigating the ensuing risks is shared between the service provider and the customer. Cloud customers must therefore understand this partition of responsibilities and face their own.
TekID’s purpose is to help organisations mitigate cyber threats and digitalisation
risks by providing business intelligence beyond technical issues. It can be to
overcome a compliance program (GDPR, CSL, ISO, SOC etc.), evaluate technology
solutions, audit your company, perform cyber forensic investigation (CFI) and cyber
threats Intelligence (CTI) or to have technology experts working side-by-side
with you.
[1] Gartner Forecast Worldwide Public Cloud Revenue to Grow 17.5 Percent in 2019, Gartner, 2nd April 2019, viewed 18th July 2019, <https://www.gartner.com/en/newsroom/press-releases/2019-04-02-gartner-forecasts-worldwide-public-cloud-revenue-to-g>
[2] Stalcup, Katy, AWS vs Azure vs Google Cloud Market Share 2019: What the Latest Data Show, ParkmyCloud, 30th April 2019, viewed 18th July 2019, <https://www.parkmycloud.com/blog/aws-vs-azure-vs-google-cloud-market-share/>
[3] Darrow, Barb, Cloud Is Secure If You Do Your Part, Says Microsoft Cloud Chief, Fortune, 7th June 2017, viewed 18th July 2019, <https://fortune.com/2017/06/07/cloud-is-secure-says-microsoft-cloud-chief/>
[4] Is the Cloud Secure?, Gartner, 27th March 2018, viewed 18th July 2019, <https://www.gartner.com/smarterwithgartner/is-the-Cloud-secure/>
[5] Breach Level Index H1 2018 Infographic, Gemalto, 2018, viewed 18th July 2019, <https://safenet.gemalto.com/resources/data-protection/breach-level-index-2018-h1/>
[6] British Airways Faces Record £183m Fine for Data Breach, BBC, 8th July 2019, viewed 18th July 2019, <https://www.bbc.com/news/business-48905907>

Recent Comments