China’s cybersecurity regime has become increasingly sophisticated over the past few years, with one of the latest regulations focussing on cross-border data transfer (CBDT), namely the Measures of CBDT Security Assessment (Measures). This article by Aaron Finlay, Tina Deng and Vivi He of Deloitte China introduces some basic concepts in the context of CBDT in China, explores the core requirements and implications of the Measures, and suggests how European companies operating in China should respond to them.
Basic concepts in the context of CBDT in China
The Measures has a total of 20 articles, covering scope, assessment trigger criteria, the assessment process and required materials, among other aspects, and serves as a reference for companies that might engage in CBDT activities. The Measures are intended to regulate the CBDT activities of personal information and critical data, protect these data and promote the security of CBDT.
There are a few concepts in the context of CBDT in China that need to be clarified, including the following:
- Personal information: This refers to any information produced by a particular natural person in its activities and that can be used to identify a particular natural person (name, address, date of birth, identification (ID) number).
- Sensitive personal information: This is any information that is particularly sensitive and may bring significant risks to the rights and interests of the personal information subject (financial information, medical records, biometric data).
- Critical data: This covers any electronic data that may endanger national security or the public interest once tampered with, destroyed, leaked, or illegally obtained or used.
- CBDT: The following scenarios are all considered as CBDT in Chinese regulations: a) foreign organisations or person accessing or viewing personal information gathered in China, even though the data is stored within China; b) providing personal information or other critical data to entities located in China, but not registered or under the jurisdiction of China; and c) transferring organisations’ internal data to foreign territories, including personal information or other critical data collected and processed.
Core requirements in the Measures
The following questions will be of concern for most companies: Do we need to complete the security assessment? If yes, what is the security assessment process and what types of materials do we need to prepare? The answers can be found in the following section.
Question 1: Do we need to complete the security assessment?
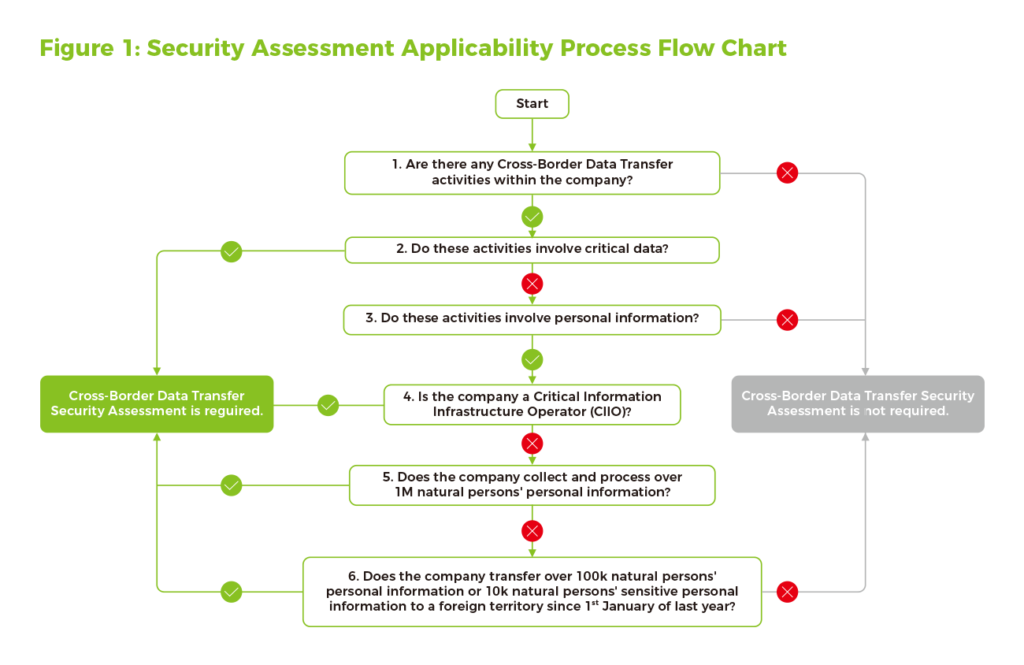
Article 4 of the Measures clarifies under which circumstances a security assessment will be triggered. If any one of the following conditions is met, companies should report to the central Cyberspace Administration of China (CAC) through its provincial branches to declare a security assessment:
- Data type: if the CBDT activities involve critical data or fall under certain conditions, or involve personal information.
- Company type: if the company is a critical information infrastructure operator (CIIO) or a data processor handling personal information of more than one million natural persons and transferring it overseas.
- Amount of data: if the company is a data processor that has transferred the personal information of over 100,000 natural persons overseas, or sensitive personal information of over 10,000 natural persons overseas since 1st January of the previous year.
Question 2: What is the security assessment process?
Articles 5 to 13 of the Measures stipulate the security assessment declaration process, which could last more than 57 business days and involves multiple supervision bureaus, such as both the provincial and national CAC. To start with, companies need to perform a self-assessment against the CBDT risks. Then, if applicable, they should report to the national CAC through the provincial CAC for a security assessment. The CAC will determine if they accept the application and conduct the assessment. If a company passes the assessment, it can perform CBDT activities within the valid period. If it fails, it can apply for reassessment or must terminate those CBDT activities. For more details on s the security assessment process, please refer to Figure 2.
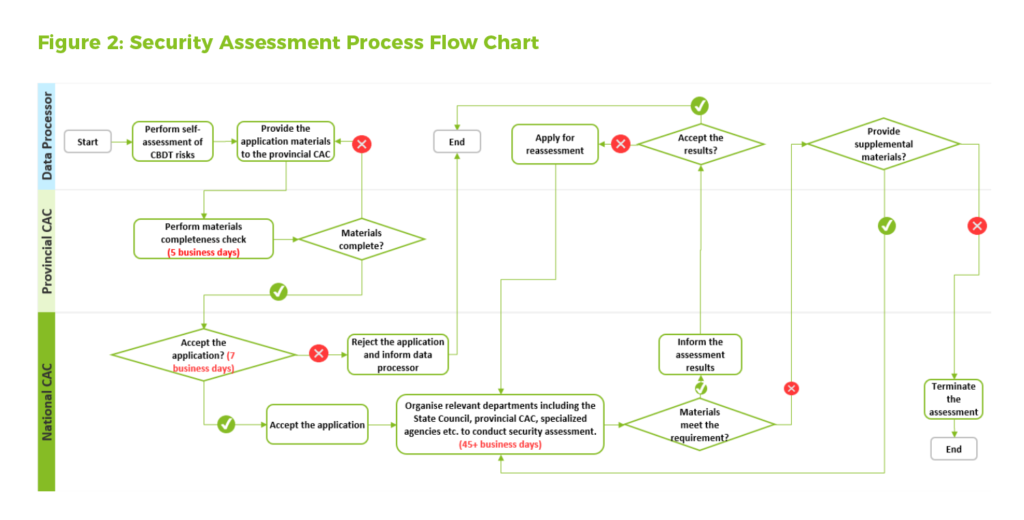
Additionally, Article 6 of the Measures indicates that the following materials are needed to declare a CBDT security assessment: 1) report statement, 2) CBDT risk self-assessment report, 3) signed legal documents between the data processor and overseas recipients, and 4) other material deemed necessary.
How should companies respond and react?
To comply with CBDT regulations, companies should plan for both short-term responses and long-term solutions.
In the short-term, companies should first evaluate if the CBDT security assessment is applicable to them. If yes, the following four steps should be taken:
- Step 1: Establish a ‘war footing’ working group and prepare all necessary resources. A Measures response team that can provide the necessary resources and make quick decisions should be immediately assembled. This team should be composed of three different roles: leaders, who provide resources and make decisions; coordinators, who are responsible for responding to the Measures and coordinating between different departments; and supporters, who are from different departments and provide the necessary departmental supports.
- Step 2: Identify CBDT business scenarios and sort out CBDT business flow. Before a self-assessment is performed, companies need to understand 1) what their CBDT scenarios are, 2) what data are transferred overseas, 3) who the data senders, transit parties and recipients are, 4) what is included in the agreement with the relevant parties, and 5) what management or technical controls are implemented with the relevant parties.
- Step 3: Perform self-assessment of CBDT risks and remediation (if any). Regional and industry-related laws and regulations should be taken into consideration. Comprehensive assessments of the legal documents, management capabilities and technical capabilities of the data senders and recipients are necessary. It is also important to consider the legality, legitimacy and necessity of the CBDT activities. Last but not least, based on these assessments and analysis, act fast and remediate.
- Step 4: Collect materials and file to the CAC. After the remediation, collect the necessary materials. Follow the security assessment declaration process specified in the Measures and file to the CAC. If the CAC rejects the request to perform CBDT activities, determine if it is necessary to apply for a reassessment.
CBDT security assessment is not a one-time activity, but more of a long-term mechanism that should be incorporated into a company’s data security governance. According to Article 14 of the Measures, when the two-year validity period of the security assessment expires, or new scenarios arise that impact data security, companies need to apply for reassessment. A company should consider the following when designing a long-term CBDT security mechanism:
- Perform data classification. CBDT is part of data security management, therefore before considering transferring the data overseas, think about localisation based on the classification of the data.
- Optimise the data security and privacy compliance management system and establish a CBDT assessment process. Optimise the existing management system based on China’s regulatory landscape and incorporate a CBDT management process, based on the Measures.
- Design data security technical solutions to ensure data security in the CBDT process. Based on the data life cycle as well as data classification, implement different technical solutions at different stages.
Note: This article has been prepared by Deloitte China for general reference only. We recommend that readers consult a risk advisor before taking action on the relevant information.
Aaron Finley is the director for South China Business Development with Deloitte China, and a board member of the European Chamber South China Chapter. Tina Deng is partner with the Deloitte Risk Advisory Cyber Team with over 16 years of professional experience. She has extensive experience in data security and privacy data protection compliance consulting. Vivi He is partner with the Deloitte Risk Advisory Cyber Team with over 18 years of professional experience. As the leader of Deloitte’s privacy protection group for Asia-Pacific in China, she is dedicated to global privacy compliance and cross region corporation.
Deloitte China provides integrated professional services, with our long-term commitment to be a leading contributor to China’s reform, opening-up and economic development. We are a globally connected firm with deep roots locally, owned by our partners in China. With over 20,000 professionals across 30 Chinese cities, we provide our clients with a one-stop shop offering world-leading audit and assurance, consulting, financial advisory, risk advisory, tax and business advisory services.

Recent Comments